📌Wallet Generation Technology
Alien supports users in generating their own cryptocurrency wallets, securing digital assets. Users can choose to generate different types of wallets, including multi-signature wallets, custodial wallets, non-custodial wallets, and MPC (Multi-Party Computation) wallets.

Wallet Encryption Systems
Multi-Signature Wallets: Requires multiple keys to authorize transactions, enhancing security. Suitable for scenarios where enterprises or teams need multi-party authentication for important transactions.
Custodial Wallets: In this wallet mode, the user's keys are managed and stored by Alien or a trusted third-party institution, suitable for users unfamiliar with encryption technology or those who prefer to delegate security management to professional institutions.
Non-Custodial Wallets: Users have full control over the wallet keys, with no intermediary involvement. This wallet offers the highest level of control and privacy protection but requires users to handle all security measures themselves.
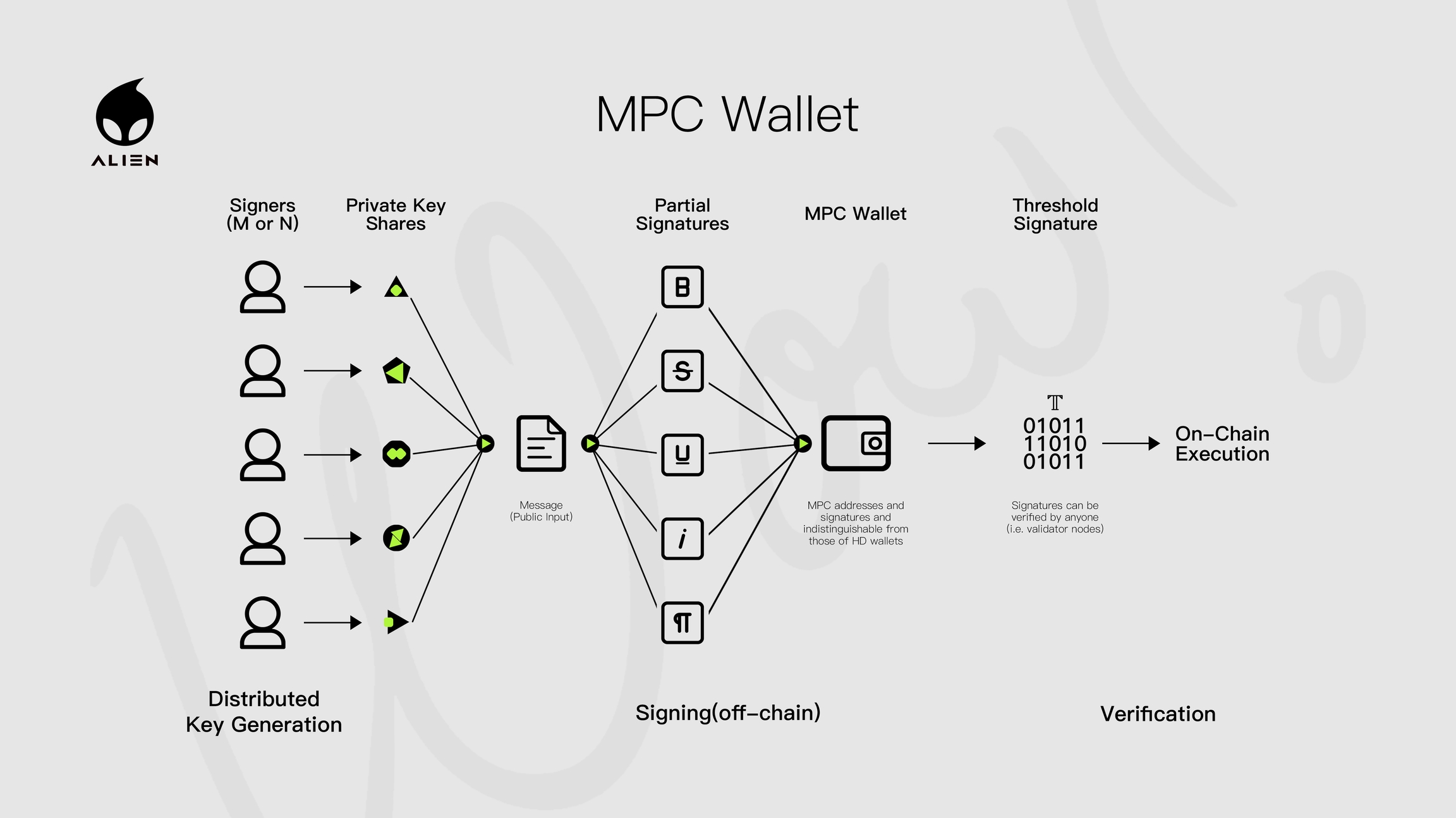
MPC Wallets: Uses multi-party computation technology to distribute key generation and management across multiple independent computing entities. This not only increases the wallet's security but also makes key management more flexible and reliable.